After importing a project, FOSSA provides an alternative way integrate build and code analysis called "Provided Builds".
In this model, FOSSA will no longer the run analysis of your first-party code from within the service. Instead, you will provide a pre-configured build environment and run a plugin built by FOSSA to analyze and upload dependency data from your build tasks.
By using this approach, you can take advantage of your CI / dev environments for dramatically faster, more accurate and reliable dependency reports, regardless of how large and complicated your build is.
During Alpha, Provided Builds are only available to certain users.
If you would like access to opt-in to Provided Builds, please contact support@fossa.io.
Provided Builds are enabled on a project-by-project basis. To start, import or pick a project that you'd like to integrate and follow the steps below:
Navigate into Project > Settings > Builds & Languages and click "Enable Provided Builds".
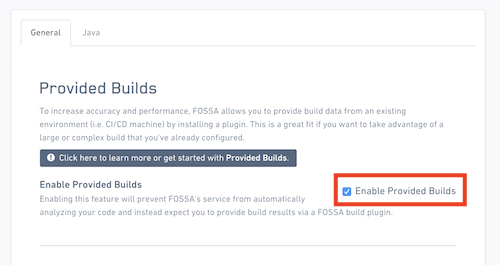
Then, click on "Save" to submit.
Once finished, FOSSA will no longer automatically run builds and scans on your code, but instead wait for data to be "provided" by your build.
fossa Build PluginThe FOSSA build plugin (fossa) is a lightweight CLI tool that interrogates an existing build environment for third-party code and uploads them to FOSSA for deeper analysis. It runs on all major platforms including Linux (Unix), OSX (Darwin) and Windows.
Run the following command from within your terminal or CI machine to get the latest version:
CLI is only available to beta users; contact support@fossa.io to apply.
Then, add it to your PATH or transfer it to the root directory of the repository you want to anaylze. To test your installation, simply run fossa and look for this message:
CRITICAL no modules specified for analysis
NOTE: We reccomend only invoking fossa from within a git repository for now.
.fossa.ymlIf you don't already have an API key, generate a token using the instructions here.
Then, in the root directory of your repository, create a .fossa.yml or .fossa.yaml file with the following layout:
version: 1
cli:
# NOTE: we recommend you set this via the FOSSA_API_KEY environment variable
api_key: some-key-here
# # Defaults to https://app.fossa.io, replace if you are on-prem
# server: https://fossa.on-prem
analyze:
modules:
- name: example-gopackage
path: github.com/orgname/full/path/to/example-gopackage
type: gopackage
# # Examples of all other currently-supported module types:
# - name: example-js
# path: package.json
# type: commonjspackage
# - name: example-ruby
# path: module/Gemfile
# type: rubygem
# - name: example-java
# path: example-java/pom.xml
# type: mavenartifact
# - name: example-bower
# path: bower.json
# type: bowerpackage
# - name: example-php
# path: composer.json
# type: composerpackage
Before running, you must explicitly define which modules you want to scan in the following format:
module/package.jsonOnce done, simply running fossa should succeed and generate a report link for your first Provided Build!
⣾ Uploading build results (2/2)...
============================================================
View FOSSA Report:
http://app.fossa.io/projects/{LINK_TO_REPORT}
============================================================
Troubleshooting:
fossa on an unpublished branch / revision, the dependency analysis will succeed but upload will fail.git repo, fossa will infer the project name, version and ID from git. If this is unavailable, you must pass the --locator flag with the revision ID (i.e. git+github.com/org/repo$revision_hash).cli.api_key and cli.server are configured to point at your local FOSSA server.Documentation for the full .fossa.yml config is coming soon.
To update a project using Provided Builds, you must invoke fossa continuously as new revisions are published through a CI or Build Machine. The typical fully-integrated workflow looks something like this:
fossa runs and analyzes artifact/build environment AFTER build successfossa uploads build results to be analyzed and scannedlicense-cli), one of which checks for scan status from FOSSA and fail a build if issues are foundCurrently you must manually add a step to your build to invoke fossa. Later on, tool-specific wrappers will be available for fossa to provide a better experience for select common integrations (i.e. Jenkins, Bitbucket, Gitlab).
Contact us if your workflow diverges from this dramatically.
Considerations:
fossa requires a build to have succeeded before it is invoked. Ideally, you provide the build command and fossa runs after it finishes. If you want fossa to run a default build command for you, you can specify the --install flag.git is unavailable, you can configure the revision to publish to by specifying its ID via the --locator flag.FOSSA_API_KEY as an environment variable rather than embedding it into the .fossa.yml file.Most users will notice a significant increase in performance and reliability after integrating Provided Builds, enabling a smoother experience when running within the development and triage workflow. This is for a few reasons:
In addition, users will experience much higher accuracy within reports and issue scans. When using Provided Builds, FOSSA's analysis operates within your existing build to get a perfect replica of your build configuration and behavior.
This permanently resolves a variety of false positives from the following sources that affect build behavior:
On top of this, explicit module definitions allow you to skip irrelevant modules that aren't built and bundled (i.e. documentation or test modules). Integrating Provided Builds can often reduce false positives by over 90%.
During Alpha, there are current limitations to Provided Builds that our team is actively addressing:
fossa plugin.